Last week I discovered a leak that effects documents published on Workplace from Facebook. After filing a white hat report, I got a response from Facebook’s security team. It seems that they are not concerned that customer data are exposed publicly by their platform via public content delivery networks. The leak is how this platform treats documents and how sharing works.

Workplace from Facebook – marketing statement on their web site
“Access for everyone” and “discover the secrets of connected companies” are taken literally.
Symptom of the leak
Like many other social networks for companies, Workplace allows sharing documents with your co-workers. Documents that only intended for internal use.
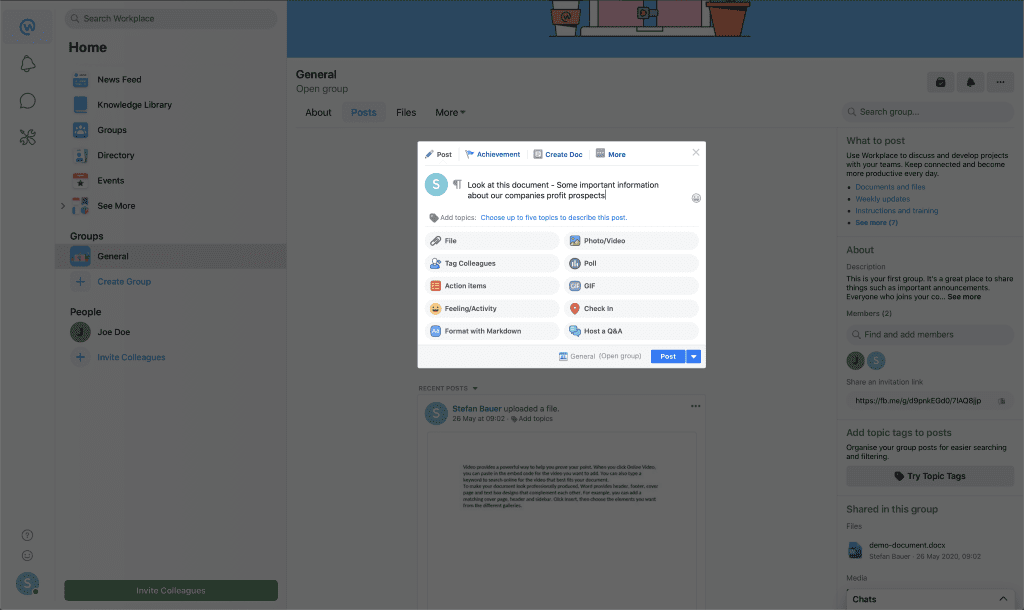
Creating a post on Workplace from Facebook
When the document gets attached to a post, a screenshot of the first page of a document gets created.
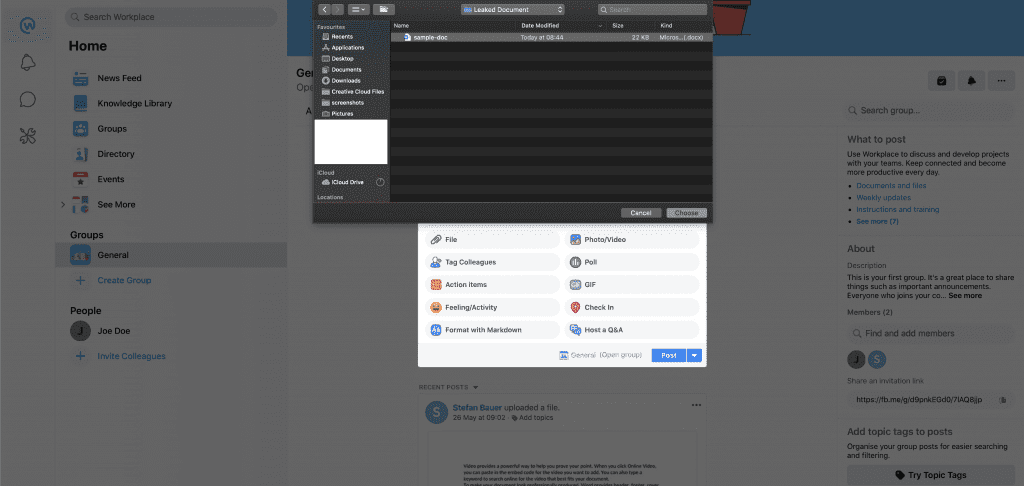
Uploading a document to Workplace from Facebook
This screenshot also gets stored in the Workplace environment. There is nothing wrong about functions like this when the screenshots get stored in a secure location and are not publicly available.
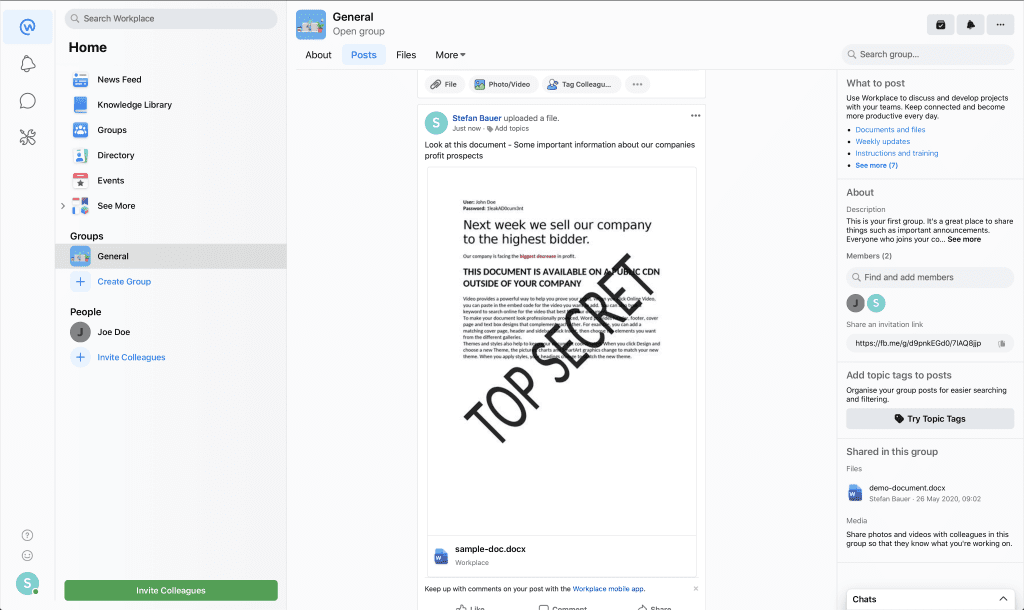
First page captured by Facebook
In case of Workplace the screenshots of the first page are stored on a public CDN without any access restrictions.
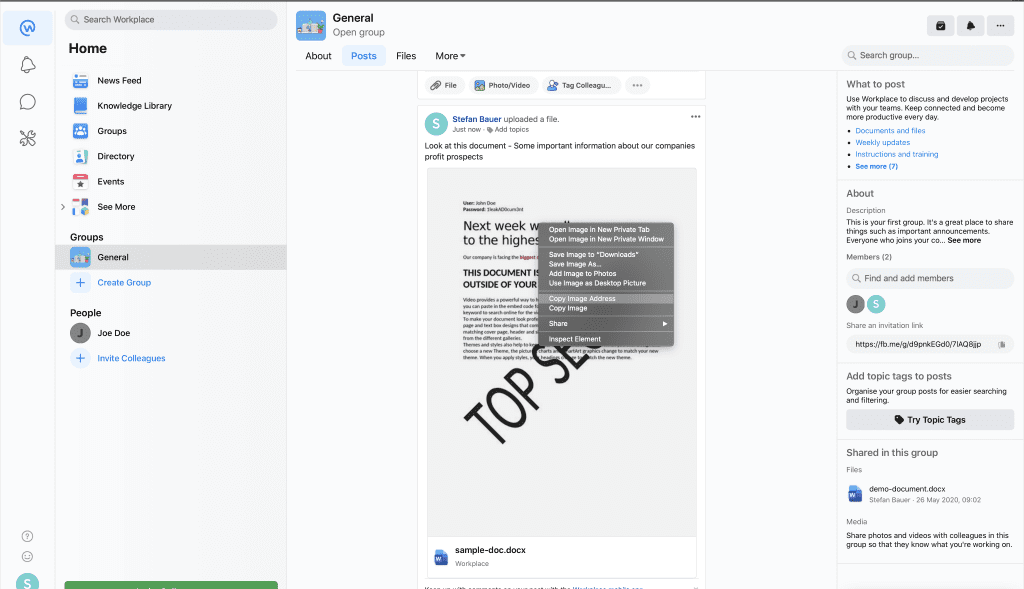
Inspection of the screenshot location
The storage location of this screenshot can be retrieved simply by inspecting the image. For example, through copy the image location and open in another browser that never have opened this image ever.
To be sure that not a local stored or cached version of this screenshot causes this effect, I opened a session on a browser testing tool that provides every time with a new browser instance from a clean virtual machine without any browser cache.
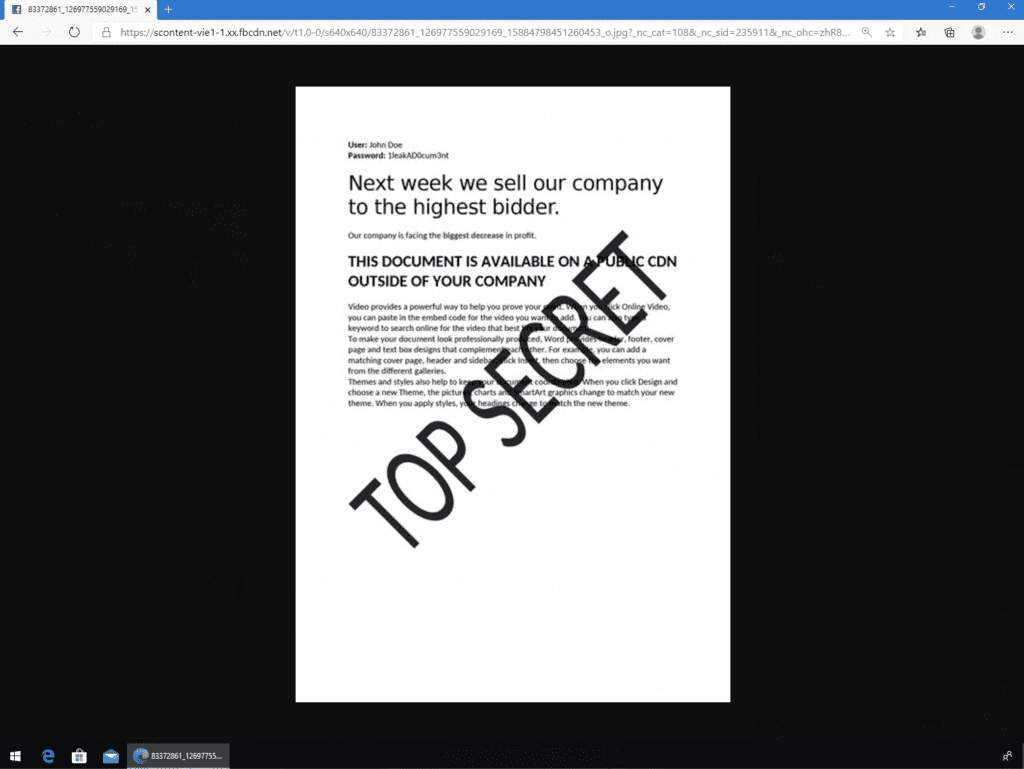
Screenshot of Document preview opened on a clean browser without cache
The image shown on the screenshot was opened without any authentication or authorisation by the owner. This first page is available to anyone.
To open this image shown before follow the following link:
Update: Link does not work anymore because Facebook disabled this account.
https://scontent-vie1-1.xx.fbcdn.net/v/t1.0-0/s640x640/83372861_126977559029169_15884798451260453_o.jpg?_nc_cat=108&_nc_sid=235911&_nc_ohc=zhR85t8WUCkAX_hrL_V&_nc_ht=scontent-vie1-1.xx&_nc_tp=7&oh=bcd3e5197774fbce230778de5f40327f&oe=5F0F44DE
As shown here, the abstract is easy to read, and the captured image has a proper resolution. As it seems this leak mostly apply to PDF, Word Documents, Google Docs as well as images shared on Workplace.
Any service connected with Workplaces from Facebook is likely to leak screenshots like this. Services like Google Docs, Office 365, DropBox, Box, to name some. The following screenshot is the content of a private document on Google, for example.
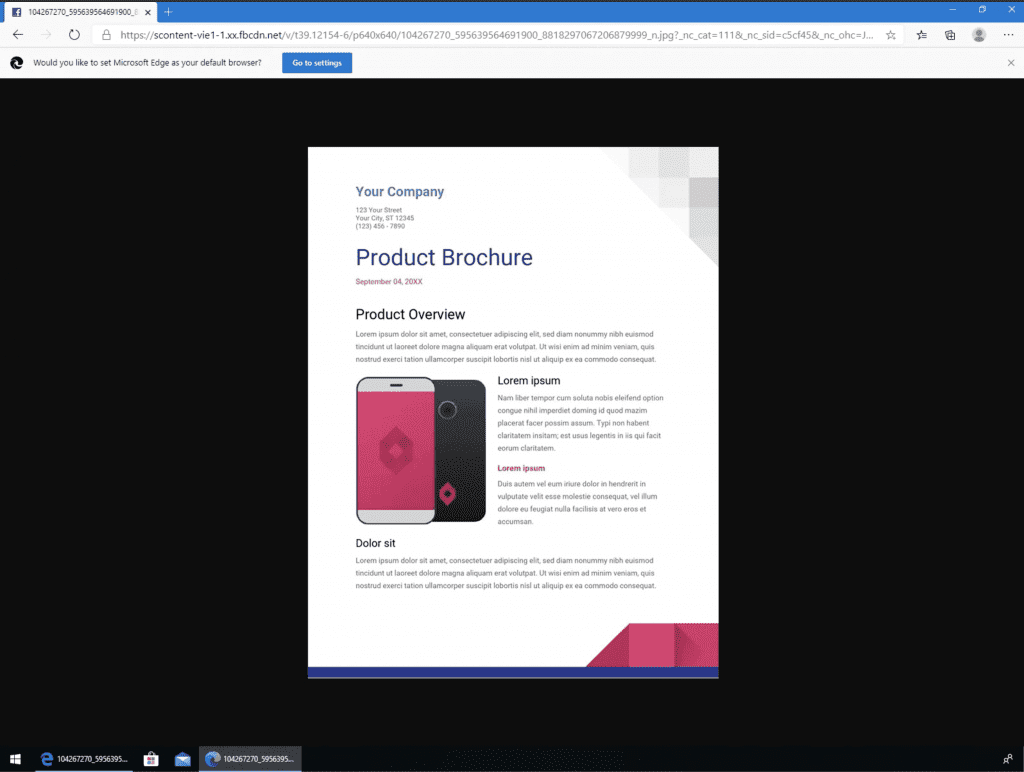
Preview capture of Google Docs document

Preview capture of Google Docs document
This leak is possible through piggybacking on the user permissions and credentials on the connected platforms and sharing the first page publicly on the publicly available content delivery network. Even someone that doesn’t have access to the document gets some information on about the document. The data is not only accessible inside an organisation but for everyone in the world.
Privacy settings on groups
Workplace for Facebook offers the following privacy settings.
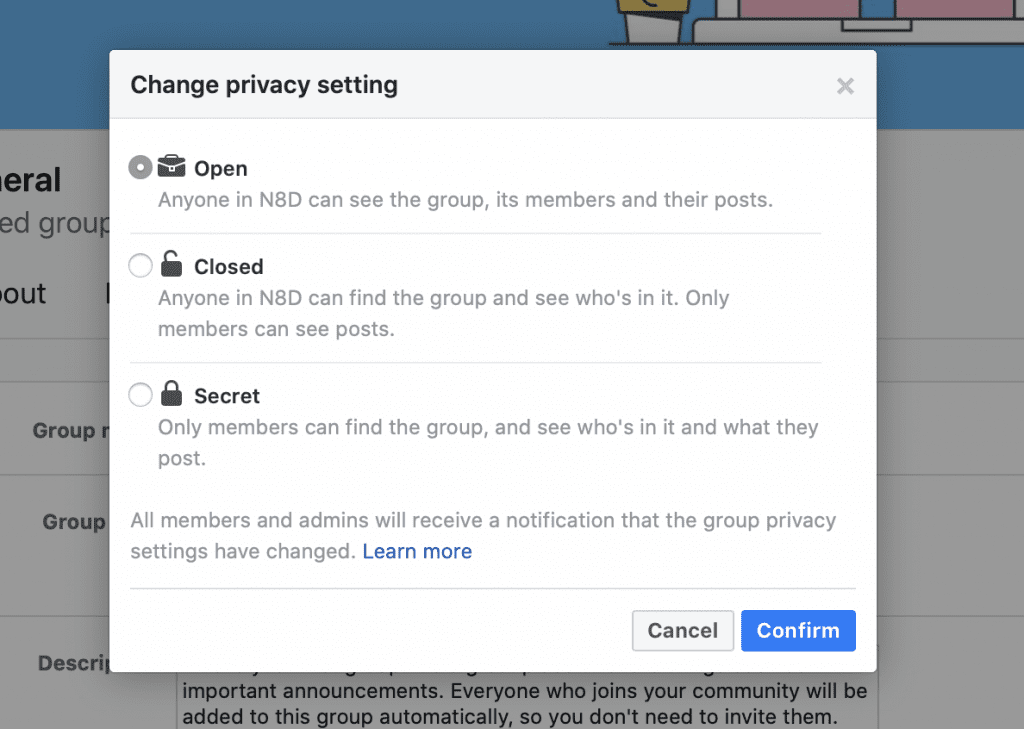
Privacy settings of Groups
In fact these setting will not get applied to the screenshots those still remain on a public CDN. If a posted document shows a preview then this preview comes from a public CDN. During multiple test it seems that sometimes a preview will not get created. Also worth noticing sometimes the preview get generated with a deloy for some minutes.
Facebooks response
This security and privacy issue got reported as a Facebook white hat security report the included a video, the general concerns as well as steps to reproduce this issue. Facebook responded with the following statement.
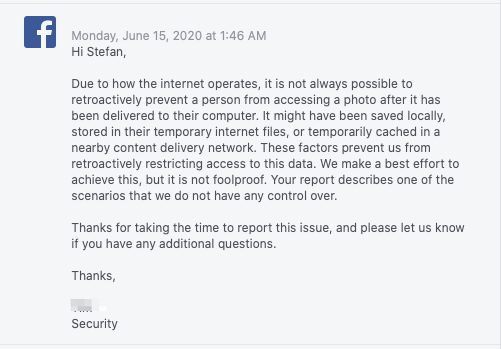
Facebooks response
Even though there is the possibility when you have access to a computer that downloaded the information, there is no reason to store company data that supposed to stay internal to put them on a public content delivery network.
Especially when the data are available more than ten days, for now, I am not saying that this feature is not useful, but the data on the screenshot should get handled with the same restrictions as the document itself. Even after the deletion of the post and the document screenshot remained on the CDN.
It is also interesting that Facebook itself stores all pictures uploaded by users on public CDN’s all over the world. Someone else likely has the privately shared photos of your children too in the worst case.
I tried to reach out to Facebook after their first response again, raising concerns again how data get handled. So far, after a couple of days waiting, I haven’t received any follow-up. It is technically possible to avoid sharing this kind of information publicly and restrict access to only their services.
Facebook does not feel any need to do so, allowing people without good intentions to harvest images and confidential information from Facebook and Workplace from Facebook.
Update 23/09/2020:
Facebook is aware of this security and data leakage issue but refuse to fix it for the good of their users and businesses. Issue is still existent but won’t get fixed. It is like always a personal decision who to trust with their data.
Also published on Medium.